Introduction
The Internet is a wonderful resource for students and teachers everywhere. Our client, Mr. Brad Budinger, is a teacher who like to use the Internet to help his students learn as well as provide them a resource to research any and all subjects. Unfortunately the Internet doesn’t just have useful learning content, it has Facebook and Myspace, flash games galore, and some very school inappropriate content. Not only are there many sites which simply aren’t relevant to school, it can be difficult to find the sites that are relevant and contain truly useful information. On this note, good sites are difficult to share, between students, and from teacher to students. Sharing options are limited to writing a URL down, or telling a search path, which may change. These are just a couple factors that make the Internet less useful than it possibly could be.
Often the Internet is used for research as well. Research can be very difficult to keep track of since there are so many web pages that get visited. This is another area where it seems there is opportunity for improvement, the ability to track and keep track of useful web pages and notes associated with them in order to make time spent on the Internet more efficient and productive. Overall, Mr. Budinger is seeking a application which will make Internet usage in the classroom, more controlled, more targeted, and more efficient both in time and effort spent by students.
In order to address the current problems in the way the Internet is used in the classroom we propose an application which will provide many functions which will directly address Internet browsing. Tools such as notes associated with web pages, a general bibliography text area viewable alongside web pages, white listed web browsing, and a link libraries which can be targeted to subjects or age groups such as class levels. These tools will make for a simplified, efficient, web browsing experience which will be straight forward for younger students, and allow older students to take notes and record useful pages simply and with little work. Along with these browsing functionalities some other useful functionality will be included. Use accounts will be accessible from any location that has the application installed, there will be a tool which will allow for the submission of files/assignments which the teacher will then be able to download. Our application will also allow for significant control for teachers, such as controlling the white list, building libraries, and viewing students browsing history, notes, and accessing uploaded files.
We aim to build all this content into a client which will then interface with an authentication server as well as a database. The centralized database will contain all the information and data about users as well as uploaded files. The client will provide both the student and the teacher interface and allow access to notes, display the library in an easily accessible format, and provide for all normal interactions with the application. With ease of use in mind we will build an application which will become a tool teachers will want to use and students will find useful.
Architecture Overview
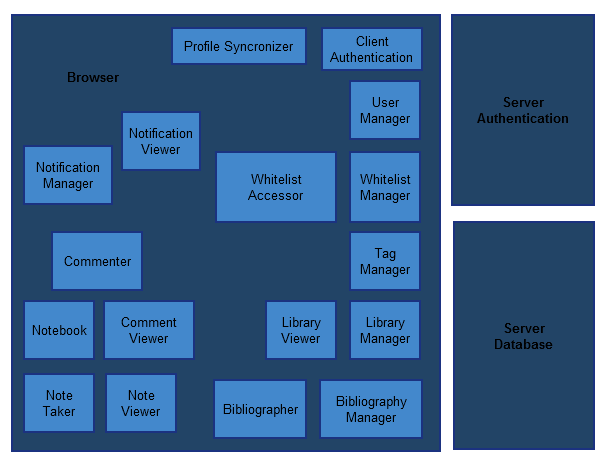
Components
|
Browser |
This component is the encompassing application that contains all client-side components. It provides a minimal web browsing user interface. |
|
Server Database |
This server component consists of a database that contains tables pertaining to all aspects of the systems operation. |
|
Client Authentication |
This component provides the interface that allows users to log in and out of the system. |
|
Server Authentication |
This server component authenticates requests from Client Authentication. |
|
User Manager |
This component allows teachers to list, add, modify, and remove users from the system. |
|
Whitelist Manager |
This component allows teachers to add, modify, and remove rules from the whitelist. |
|
Whitelist Accessor |
This component grants or denies access to URLs based on the whitelist rules. It acts on every HTTP request made by the Browser. |
|
Profile Synchronizer |
This component tracks browser history and bookmarks and records changes to the Server Database. It also restores history and bookmarks (and other profile related data) on login. |
|
Tag Manager |
This component allows teachers to list, add, modify, and remove tags from the system. |
|
Library Viewer |
This component provides a user interface for students to browse library entries (bookmarks) provided by teachers. |
|
Library Manager |
This component provides a user interface for teachers to list, add, modify, and remove library entries (bookmarks) from the system. |
|
Note Taker |
This component provides a user interface for taking notes on the current URL. This component also allows users to upload files, tag the note, or mark it public. |
|
Notebook |
This component provides a user interface for listing and sorting all notes for all URLs. |
|
Note Viewer |
This component provides a user interface for viewing notes taken by other users on the current URL. |
|
Commenter |
This component provides a user interface for making comments that are attached to notes. |
|
Comment Viewer |
This component provides a user interface for viewing comments that other users have attached to notes. |
|
Notification Manager |
This component provides a user interface for teachers to change the MOTD, or to broadcast new notifications. |
|
Notification Viewer |
This component provides a user interface for students to view the MOTD and other notifications. |
|
Bibliographer |
This component provides a user interface for adding / removing the current URL from the bibliography. |
|
Bibliography Manager |
This component provides a user interface for listing, adding, removing, and exporting bibliography entries. |
To give more detail into these modules, they are, in general, GUI components. Here are some examples as we currently see them.
Library Viewer
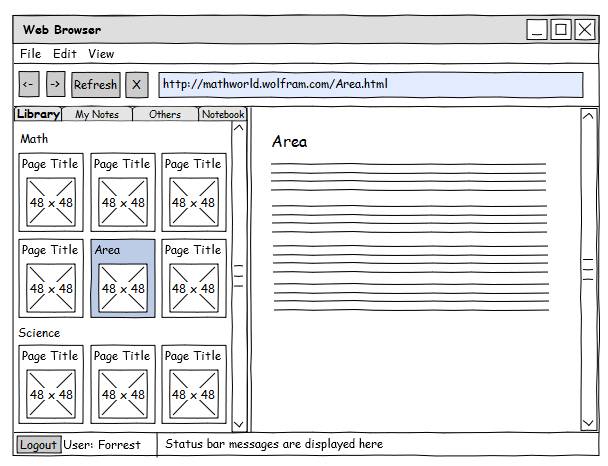
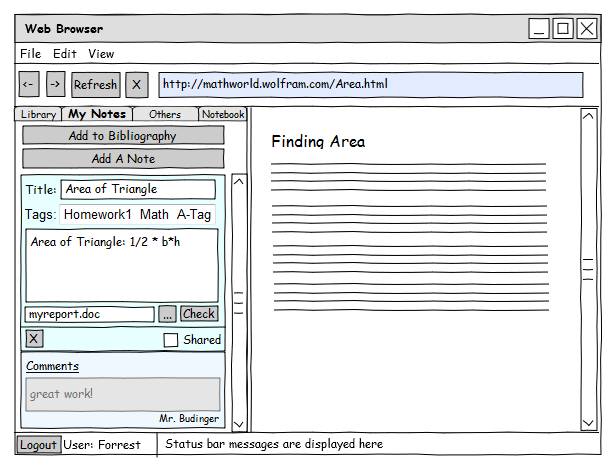
Note Taker
Bibliography
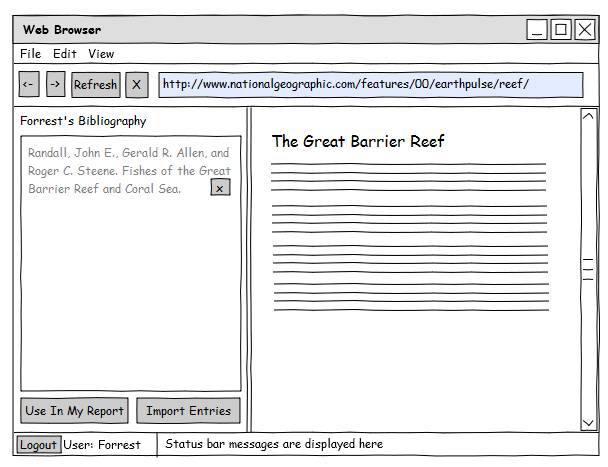
Notebook
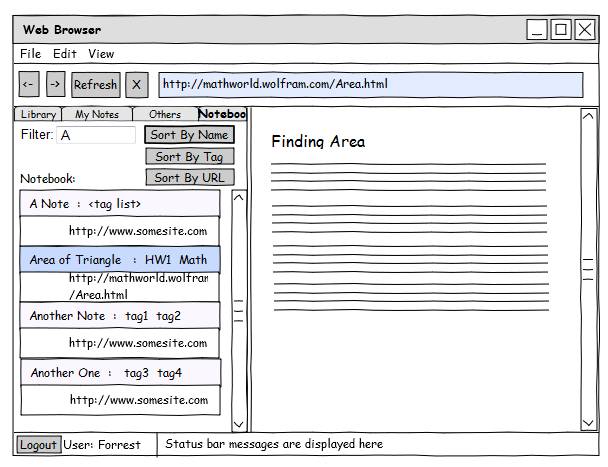
Detailed Module Descriptions
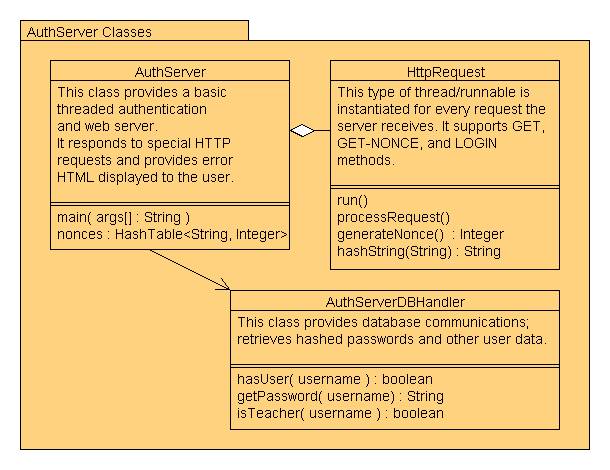
The following are descriptions of modules as we understand them currently, this means that some modules have significantly more detail than others, and that what is stated here may change during implementation. For instance, the Authentication Server already exists, hence it is described in great detail, other aspects simply haven’t had the same time or detail invested yet.
A diagram of how we currently view our overall architecture as far as distribution and data flow.
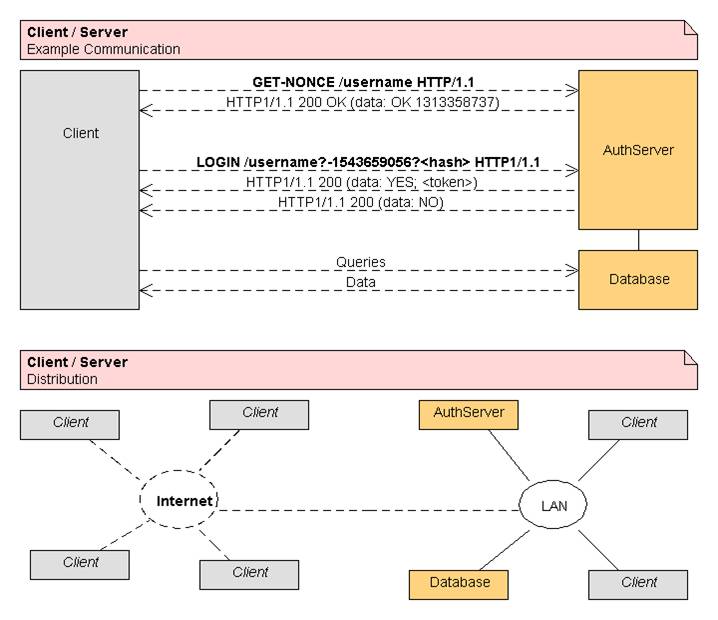
Authorization
● Server Authentication Component: this acts as the server component, listening for authentication requests and responding to them.
● Client Authentication Component: this speaks with the server component in order to determine if someone should have access to the system or not.
|
Server Authentication Component |
||||||
|
Goal: The goal of the Server Authentication Component is to authenticate users on login. It is a server that listens on a network port and responds to authentication-specific requests. These requests will take the form of modified HTTP. |
||||||
|
Functions:
|
|
Client Authentication Component |
||||||||||||||||
|
Goal: The goal of the Client Authentication Component is to authenticate users on login. It is responsible for contacting the server component with a given set of credentials. It grants access to the system after receiving an affirmative response from the server, or blocks access to the system after receiving a negative response. |
||||||||||||||||
|
Functions:
|
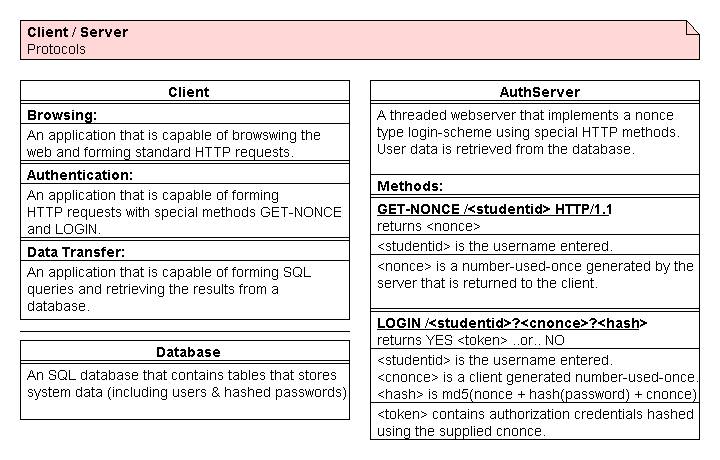
Java authentication server classes and their methods.
User-Manager
|
User-Manager Component |
||||||||||||||||||||
|
Goal: The goal of the user-manager component is to provide a user-interface for users who are teachers to list, add, modify, and remove users from the system. |
||||||||||||||||||||
|
Functions:
|
Whitelist
|
Whitelist Component |
||||||||||||||||||
|
Goal: The goal of the Whitelist component is to validate requested URLs against a valid list of URLs. A URL is either on the whitelist and valid, or not on the list and invalid. |
||||||||||||||||||
|
Functions:
|
DatabaseHandler
|
DatabaseHandler |
||||||||||||||||||||||||||||
|
Goal: Provide all required database interaction functionality. This means pulling down information as well as adding information to the database. |
||||||||||||||||||||||||||||
|
Functions:
|
Lists of fields and methods within a couple classes and and example of usage.
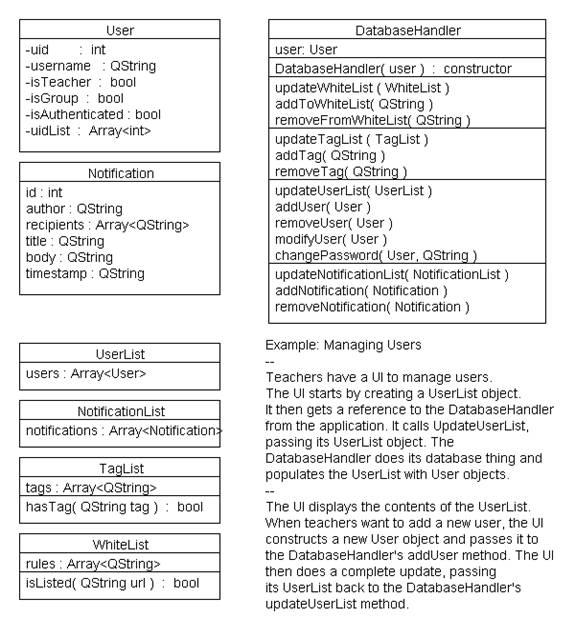
Part of this design involves several container classes to contain information from the database, as of yet these are undefined but will roughly mirror the database tables described below. An example of these classes would be Note and Notes, Notes will contain many Note objects, each of which is just a single instance of a note and URL pair. As the project progresses we will describe these classes and their interfaces. However, because of the focus on creating a working product we have sacrificed some documenting for a quick return, and because of this, already have a working web browser and shell components which are laid out to handle displaying content which will be pulled from the server.
Database Design:
Tables:
User
UID : enum
name : char
isTeacher : bool
isLoggedIn : bool
isGroup : bool
idList : char
noteID : enum
bibID : enum
The user table consists of all the users of the system. There is a uid in order to keep track of users more easily in the sytem. The name is simply for users to see names rather than an id. In order to determine if the user is a teacher or not, the isTeacher field is used. This will help determine if the user needs to see administrative functionality or not. isLoggedIn will be used to see if a user is logged in. This will be used for things such as indicating a user has an update. A user entry can also be used for a group by setting the isGroup field and listing out the id numbers of the users in the group in the idList field. The user table also contains two fields, noteID and bibID, that point to the note and bibliography tables for the user.
Whitelist
rule : char
The whitelist is simply filled with many rules for different web sites that can be visited by users. The rules can be either a URL for a specific site or a URL with the wildcard symbol (*) which indicates that anything can be placed where the wildcard symbol is and be a valid site to go to.
Library
name : char
url : char
category : char
desc : char
The library tables are used as subsets of the whitelist to create smaller views. The table contains the name, URL, and description of the site the entry is for. It also contains a category or list of categories that the site belongs to.
Bibliography
UID : enum
title : char
author : char
date : char
url : char
The bibliography table will hold a user's entries for their bibliography. It contains the UID of the user it is for, the title, author, and url of the web page, as well as the date when the web page was found. This is all stored so that the user can create a text document of the bibliography when they are done with the document or assignment.
Notes
UID : enum
isNote : bool
content : char
isPublic : bool
author : enum
title : char
filepath : char
tags : char
The notes table contains all of the notes and comments for each user. It is one table to hold both the user's notes, as well as the comments by other users on the notes. All notes and comments for a user will be given the user's id in the UID field. The isNote field will distinguish the entry between a note and a comment. The content field stores the text of the note or comment. isPublic is used to specify whether the note is viewable by all or not. The author field keeps track of who wrote the note, this could be different from the UID for comments. The title field stores the user specified title. The tags field will keep track of any tags given to the note for organization. Finally, the filepath will keep track of any files uploaded into the note for file submissions. This field won't be used right away, but will be there for later functionality.
Notifications
text : char
author : enum
recipients : char
timestamp : timestamp
The notifications table will keep all of the notifications made. Each entry will have the text of the notification, the author, the recipients, and a timestamp. The author will be a UID of the user that created the notification. The recipients will be a list of UIDs that the notification will be displayed to. The timestamp will be used for deleting old entries.
Implementation Plan
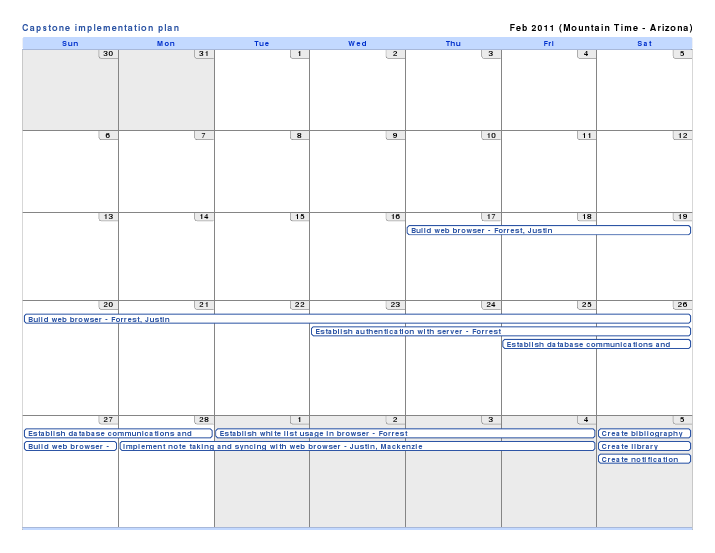
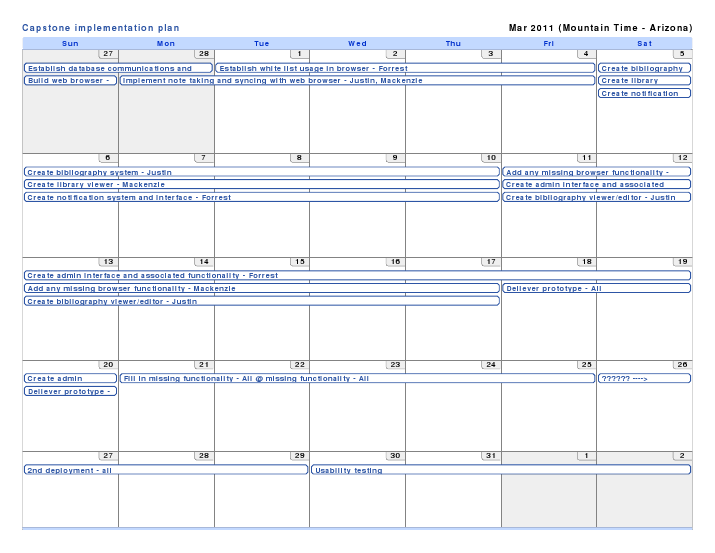
The following is a rough plan of the order in which things will get implemented, and who will be working on them. Tasks in the near future are much more accurate than plans a month out which will depend upon previously completed tasks. The big picture is we aim to have a nearly completed project by the end of March so that we may test and finish refining the application in April.
February
March
April